Which of the Following Best Describes Detective Controls
Which of the following statements best describes control environment. The entity s process for identifying business risks relevant to financial reporting objectives and deciding about actions to address those risks and the results thereof.
The 3 Types Of Security Controls Expert Explains
Audit trails The correct answer is.

. Which best describes access controls. Audit trails capture information which can be used for detecting errors. Randy agrees to work with the detective and a sting operation is set up with the cooperation of the uncle.
5 states that internal controls may be preventive or detective. Which of the following best describes authentication in the Remote Access Domain. Reduce the effect of an attack.
Only the decision diamond shows branching of the sequence flow. Internal Control 3 18 Which of the following best describes the major disadvantage of using a questionnaire rather than a flowchart to evaluate internal controls. The PCAOBs AS No.
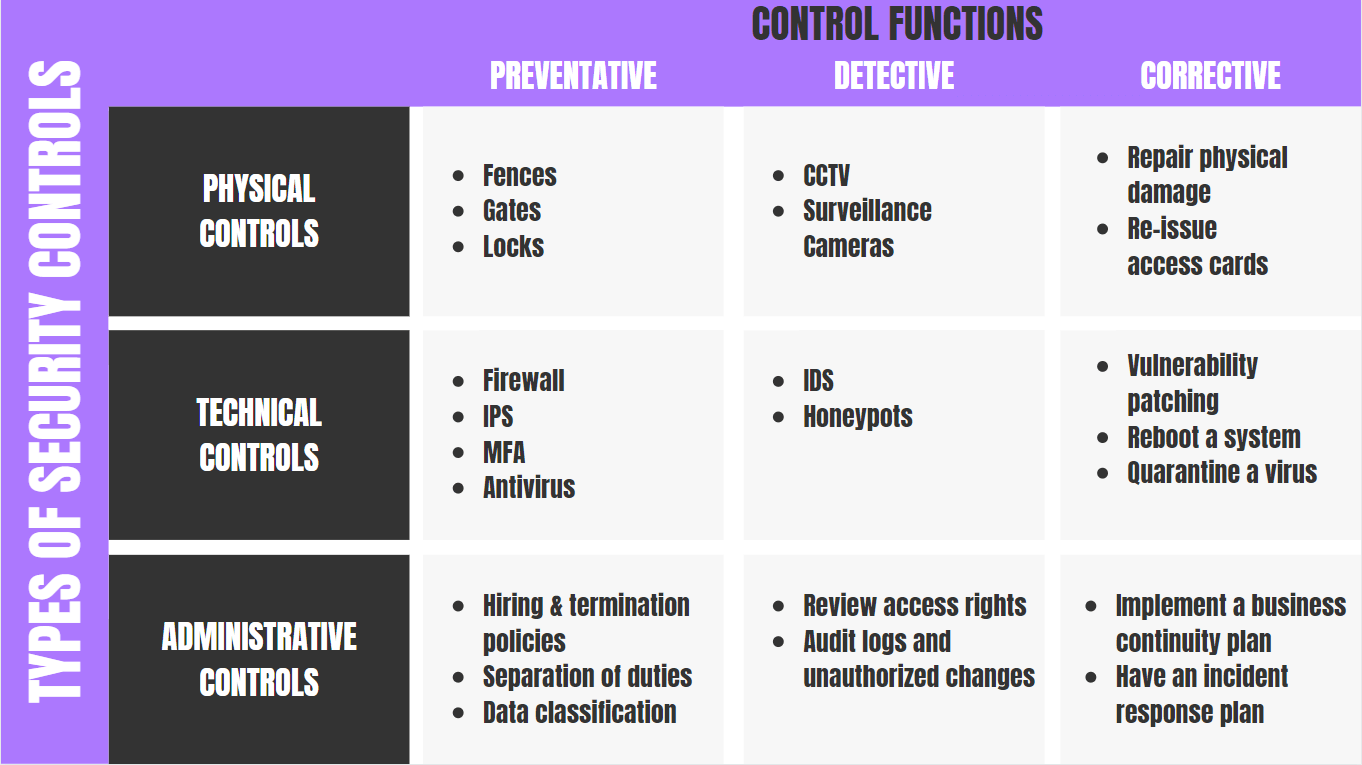
Detective controls are designed to detect a threat event once that event has occurred. Backup procedures used to archive data D. Detective controls aim to reduce the impact of such events.
Internet Protocol Security IPSec. Access controls help protect against threats and vulnerabilities by reducing exposure to unauthorized activities and providing access to information and systems to only those who. Only the gateway shows branching of the sequence flow.
Assurance from top management that computer centers are kept locked. A type of internal control mechanism intended to find problems within a companys processes. Echo controls in telecommunications.
The employment of trustworthy people to enter data into the information system. Which of the following is an example of detective controls. So the detective control detects the transposition error in the book.
Integrated auditing combines the operational audit function the financial audit function and the IS audit function. Integrated auditing places internal control in the hands of management and reduces the time between the audit and the time of reporting. Determine the control environment in the department.
Reduce the likelihood of a deliberate attack. Which of the following is not one of the four common elements needed to determine whether fraud is present. While both are after the fact A the order of application is not really relevant.
Which of the following is primarily a detective control in the Remote Access Domain. Which of the following is the best example of a detective control. Internal audits and other reviews.
Detective control may be employed in accordance with many different goals such as. There are multiple task types that may be available in this quiz. Which of the following controls is preventive.
The bank reconciliation statement is a part of the accounting process. Segregation of duties C. Mike offers Randy 10000 to kill a rich uncle.
Ensure the organization hires the right people. Requiring two persons to open mail containing payments. Randy tells a detective about the plot.
Which of the following is an example of a detective control in an information system. Quizzes allow for partial credit scoring on all item types to foster Continue. The detective control is a part of the internal control where it assists to detect the errors in the accounting book.
Examples of detective controls include the following. O2019 Gleim Publications Inc. Randy gives a picture of the contrived murder as proof of the event and asks Mike for his money.
Establish the level of compliance with controls. Which of the following best describes the purpose of personnel policies and procedures. Cybersecurity Essentials 11 Final Quiz Answers 100 2018 Quiz Instructions This quiz covers all of the content in Cybersecurity Essentials 11.
41 Which of the following best describes detective controls. Discover attack and trigger preventive or corrective controls. While corrective controls keep errors from resulting in loss B detective controls do not warn deterrent controls do.
One control is used to identify that an error has occurred and the other fixes the problems before a loss occurs. Therefore they are considered to be detective controls. The gateway does not represent a decision.
Physical access controls B. Which of the following best describes the difference between a BPMN gateway and a flowcharting decision diamond. It is designed to test the skills and knowledge presented in the course.
To prevent an attacker from capturing and reading the data. D The correct answer is D. Checkpoints in production jobs.
Multiple Choice O Management periodically determines whether the amount of physical assets agree with the accounting records The company should establish formal guidelines to handle cash receipts and make purchases Important documents should be kept in a safe place and electronic files. Which of the following best describes integrated auditing. The decision diamond can depict more branching options.
Automated reports to management that specifically identify delinquent receivables. Establish the time budget for the audit. Access controls are a collection of technical controls that permit access to authorized users systems and applications.
Access-control software that uses passwords tokens andor biometrics B.

The 3 Types Of Security Controls Expert Explains

No comments for "Which of the Following Best Describes Detective Controls"
Post a Comment